Correct identified errors
Correcting Identified Errors (Program Testing and Maintenance)
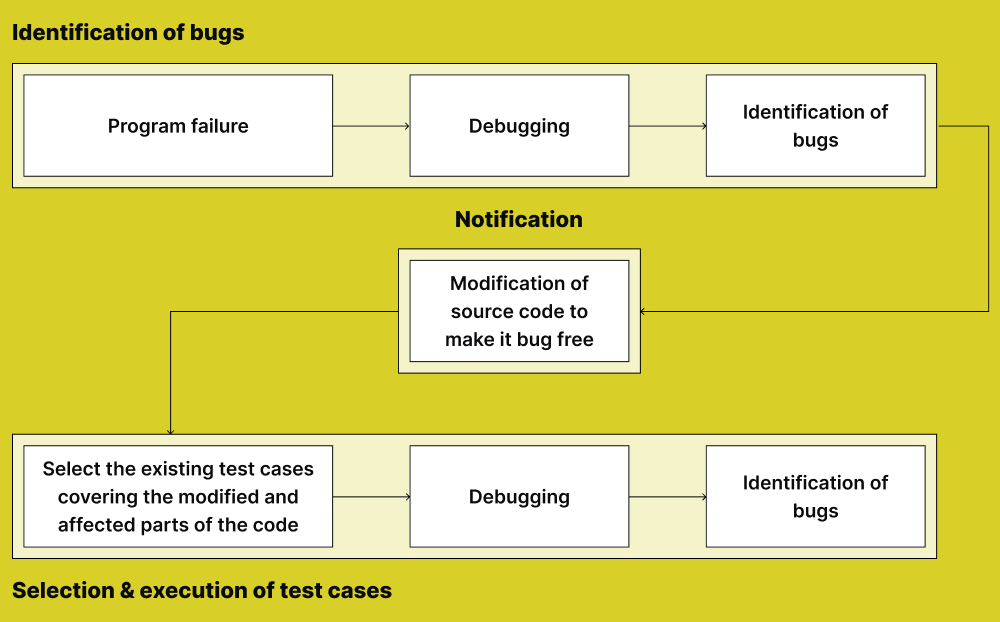
Program testing does not end when errors are found. The real value of testing comes from correcting those errors and ensuring the program works correctly afterward. This stage is part of program maintenance and debugging.
What is an Error?
An error is a flaw in a program that causes it to produce incorrect results, crash, or behave unexpectedly.
Errors are often called bugs, and the process of fixing them is called debugging.
Types of Errors That Need Correction
1. Syntax Errors
These occur when the program breaks the rules of the programming language.
Examples:
IF x > 5 PRINT x
Correction:
IF x > 5 THEN PRINT x ENDIF
These are usually detected automatically by the compiler or interpreter.
2. Logic Errors
These occur when the program runs but produces incorrect results.
Example:
area = length + width
Correction:
area = length * width
The program runs, but the formula was wrong.
3. Runtime Errors
These occur during program execution and cause the program to crash.
Example:
average = total / count
If:
\[ count = 0 \]
Correction:
IF count > 0 THEN average = total / count ENDIF
This prevents division by zero.
The Debugging Process
Correcting errors follows a logical process.
Step 1: Identify the Error
Use:
- Test results
- Error messages
- Unexpected outputs
Step 2: Locate the Source of the Error
Find the exact line causing the problem.
This can be done using:
- Breakpoints
- Debugging tools
- Tracing variables
Step 3: Correct the Error
Modify the faulty code.
Example:
total = total - price
Corrected version:
total = total + price
Step 4: Retest the Program
This ensures:
- The error is fixed
- No new errors were introduced
This is called:
Regression testing
Use of Trace Tables to Correct Errors
A trace table helps track how variables change during execution.
Example program:
sum = 0 FOR i = 1 TO 3 sum = sum + i NEXT i PRINT sum
Trace table:
| i | sum |
|---|---|
| 1 | 1 |
| 2 | 3 |
| 3 | 6 |
If output was wrong, the trace table helps find where the mistake happened.
Testing After Correction
After fixing errors, the program must be tested again using:
- Normal data
- Boundary data
- Invalid data
This ensures the correction works in all situations.
Importance of Correcting Errors
Failure to correct errors can lead to:
- Incorrect results
- System crashes
- Loss of data
- Safety risks
Example:
An incorrect calculation:
\[ \text{Total} = \text{Price} - \text{Tax} \]
Instead of:
\[ \text{Total} = \text{Price} + \text{Tax} \]
This could cause financial loss.
Maintenance After Error Correction
Correcting errors is part of:
Corrective maintenance
Other maintenance types include:
- Adaptive maintenance – modifying for new environments
- Perfective maintenance – improving performance
Summary
- Errors must be corrected after testing
- This process is called debugging
- Errors include syntax, logic, and runtime errors
- Trace tables help locate errors
- Programs must be retested after correction
- This is part of program maintenance
Exam-Style Questions
1. Define debugging.
2. Describe how a trace table helps correct errors.
3. Explain why programs must be retested after correction.
4. Identify and correct the error:
average = total / count
where count may be zero.
5. State two types of maintenance.
Create an account or Login to take a Quiz
Log in to suggest improvements to this note.